Price ranges are sometimes mentioned in Bitcoin. We converted Individuals figures to US bucks using the Trade price with the day that the value was recorded.
4 Develop your mobile device security portfolio The fourth stage is to build your mobile device security portfolio by showcasing your skills, projects, and achievements in the field. To achieve this, you must create and retain a web based profile that highlights your schooling, expertise, competencies, certifications, and publications associated with mobile device security.
A few teams claim they could Strengthen clients’ credit scores or apparent their debt. They might demand a flat sum or a share of The shoppers’ savings. One group promises it may eliminate buyers’ names from blacklists of financial loan defaulters.
You ought to look for someone who's accustomed to the software program and units that you might want them to hack. The hacker ought to be acquainted with the equipment that they're going to should execute their assaults. White hat hackers with more knowledge will Expense far more.
It is vital to conduct an intensive interview so as to ascertain a hacker’s expertise and past working experience. Below are a few queries that you could potentially question opportunity candidates.
3 Follow your mobile device security skills The third move to follow your mobile device security competencies is to use them to authentic-earth situations and issues. You are able to do this by taking part in classes, workshops, bootcamps, or certifications that concentrate on mobile device security, like SANS SEC575: Mobile Device Security and Ethical Hacking or the eLearnSecurity eMAPT: Mobile Application Penetration Tester.
For those who’ve ever applied your phone in the vicinity of another electronic device (like a TV) and discovered a distortion within the audio, While you aren’t with a phone contact, this may be a symptom that someone has hacked your device or maybe even installed hardware (a Bodily component) onto your phone.
In your usage of our Services, you agree to act responsibly inside a fashion demonstrating the physical exercise of good judgment. By way of example and devoid of limitation, you concur never to: violate any applicable law or regulation,
I used to be suspicious that someone is thieving information from my phone and somebody is checking my phone. Penticians assisted me in catching my dishonest husband or wife.
When getting started in mobile testing, it’s useful to possess a qualifications usually penetration testing, some primary programming competencies and two or three non-specialized “gentle techniques.”
Mobile application penetration testing makes it possible for companies a chance to weed out any imperfections in their network that involve instant patching and/or learn more protection. Corporations which can be getting into a mobile pen exam scenario need to concentrate on staying as positive as you possibly can and considering the test as an educational knowledge.
Tutorials Position is a number one Ed Tech firm striving to deliver the ideal Discovering material on complex and non-complex subjects.
A number of software program has become developed to automate prevalent areas of the mobile pentesting approach. The following can be an incomplete list of some of the resources accessible to the mobile-device pentester.
Exactly what are you awaiting? Speak to us right now and let us provide you with what we are able to do. We assurance which you won’t be unhappy.
 Alana "Honey Boo Boo" Thompson Then & Now!
Alana "Honey Boo Boo" Thompson Then & Now! Alfonso Ribeiro Then & Now!
Alfonso Ribeiro Then & Now! Keshia Knight Pulliam Then & Now!
Keshia Knight Pulliam Then & Now!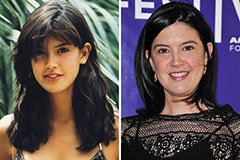 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Lacey Chabert Then & Now!
Lacey Chabert Then & Now!